[100 New Questions] Because of the change of the 70-410 exam, now more new added 70-410 exam questions and answers are available at Lead2pass. In Lead2pass new 70-410 445q vce or pdf braindump file, you can get all the new questions and answers. We guarantee the 100% pass rate.
QUESTION 181
Hotspot Question
Your network contains two servers named Server1 and Server2 that run Windows Server 2012 R2. Server1 has the Hyper-V server role installed. Server2 has the Windows Deployment Services server role installed. On Server1, you have a virtual machine named VM1.
You plan to deploy an image to VM1 by using Windows Deployment Services (WDS).
You need to ensure that VM1 can connect to Server1 by using PXE.
Which settings should you configure on VM1? To answer, select the appropriate settings in the answer area.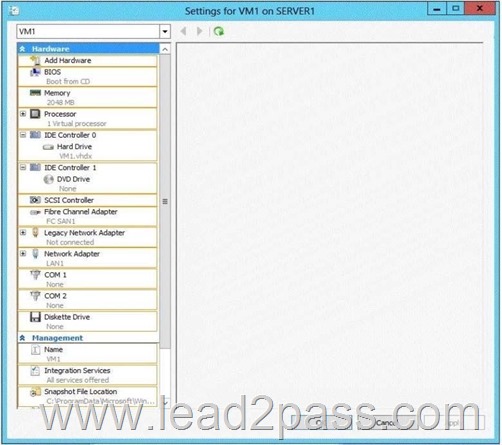
Answer: 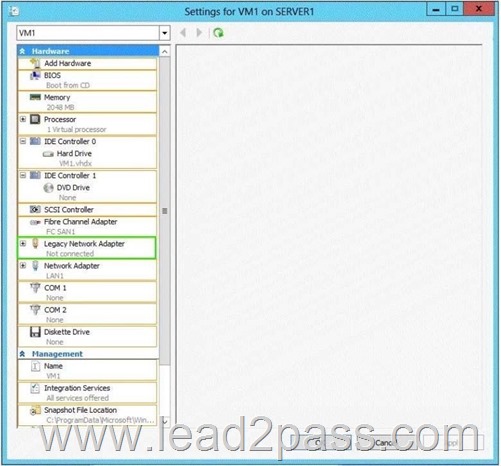
Explanation:
Virtual machines can be deployed to Hyper-V using Windows Deployment Services (WDS). To accomplish this requires the proper WDS infrastructure be in place and that the VM PXE boot using a Legacy Network Adapter. By default, there is only a “Standard Network Adapter” installed on the Virtual Machine, but for PXE functionality you will need to add a “Legacy Network Adapter”.
Go to the “Legacy Network Adapter” that you just added and specify that it should use the Virtual Switch that you just created.
Last but not least, you should change the BIOS boot priority to make sure that the Virtual Machine always tries to boot first using the “Legacy Network Adapter”.
Just select the “Legacy Network Adapter” and move it to the top using the buttons.
Start your Virtual Machine and now PXE boot should work
http://www.danielclasson.com/guide-how-to-get-pxe-boot-to-work-in-hyper-v/ http://blogs.technet.com/b/askcore/archive/2008/11/25/installing-a-vm-operating-system-using-a-legacy-network-adapter-and-pxe-boot.aspx
QUESTION 182
Hotspot Question
Your network contains an Active Directory domain named contoso.com.
You need to identify whether the Company attribute replicates to the global catalog.
Which part of the Active Directory partition should you view? To answer, select the appropriate Active Directory object in the answer area.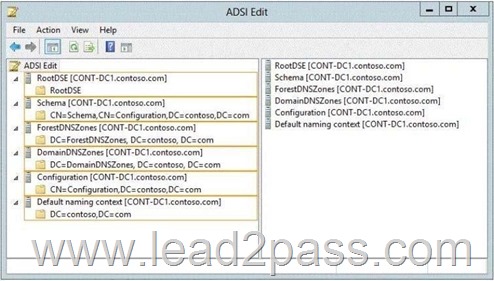
Answer: 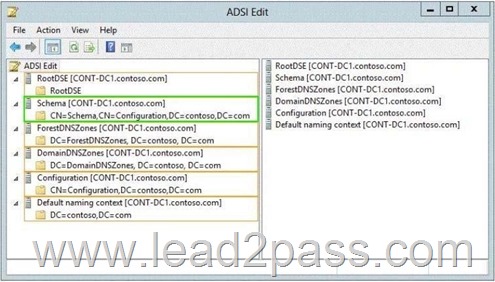
Explanation:
Schema -Contains the Schema container, which stores class and attribute definitions for all existing and possible Active Directory objects in cn=schema,cn=configuration,dc= forestRootDomain . Updates to this container are replicated to all domain controllers in the forest. You can view the contents of the Schema container in the Active Directory Schema console.
http://technet.microsoft.com/en-us/library/cc961591.aspx
QUESTION 183
Hotspot Question
You have a server named Server1. Server1 runs Windows Server 2012 R2 and has the Windows Deployment Services (WDS) server role installed.
You install the DHCP Server server role on Server1.
You need to ensure that Server1 can respond to DHCP clients and WDS clients.
What should you configure for the DHCP service and the WDS service?
To answer, configure the appropriate options in the answer area.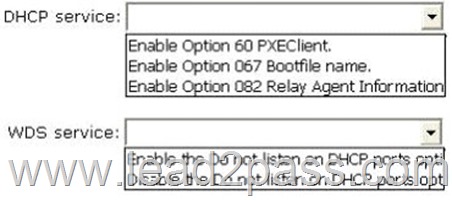
Answer: 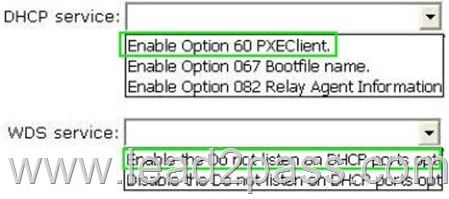
Explanation:
Traditionally, only DHCP listened on port UDP 67, but now WDS also listens on port UDP 67 WDS and DHCP are installed on the same server: You must tell WDS not to listen on port UDP 67, leaving it available for DHCP traffic only. But then how does the client find the WDS server? You set option 60 in DHCP.
The DHCP option 60, when set to “PXEClient” is used only to instruct the PXE clients to try to use a PXE Service bound on UDP port 4011. Actually, if there is a bootp or dhcp service bound on UDP port 67 of an host (usually called a server), a PXE service cannot bind on that port on that host. Since the PXE Service uses BOOTP/DHCP packets to send the options 66 and 67 to the clients, it needs to be able to bind to the associated port (bootps) or to an alternated port (4011) that the clients know they must use as the alternate port. And to instruct the clients to use this alternate port, you have to set dhcp option 60 to “PXEClient”.
If Windows Deployment Services and DHCP are running on the same computer, configuring Windows Deployment Services to not respond to any client computers will not work. This is because although Windows Deployment Services will not respond, DHCP will. You should disable WDS if you have both installed and using DHCP.
To configure Windows Deployment Services to run on the same computer as Microsoft DHCP
Right-click the server and click Properties.On the DHCP tab, select Do not listen on port 67 and Configure DHCP Option #60 Tag to PXEClient.
This procedure does the following: Sets
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\WDSServer\Parameters \UseDhcpPorts to 0. Adds the option 60 PXEClient tag to all of your DHCP scopes.
http://gallery.technet.microsoft.com/DHCP-Option-60-Configuratio-2cad825d
QUESTION 184
Hotspot Question
You have a server named Server1. Server1 runs Windows Server 2012 R2. A user named Admin1 is a member of the local Administrators group.
You need to ensure that Admin1 receives a User Account Control (UAC) prompt when attempting to open Windows PowerShell as an administrator.
Which setting should you modify from the Local Group Policy Editor? To answer, select the appropriate setting in the answer area.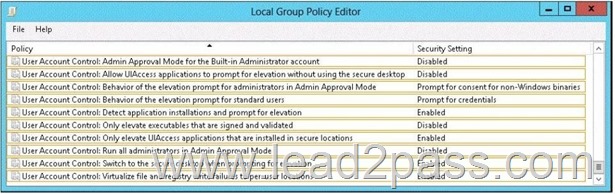
Answer: 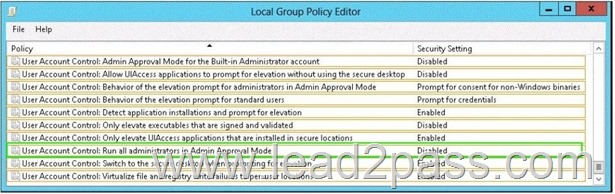
QUESTION 185
You have a server that runs Windows Server 2012 R2.
The server contains the disks configured as shown in the following table.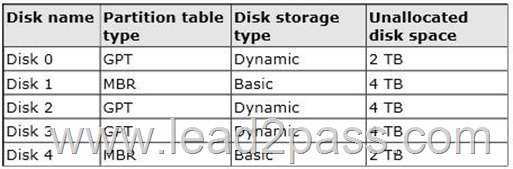
You need to create a volume that can store up to 3 TB of user files.
The solution must ensure that the user files are available if one of the disks in the volume fails.
What should you create?
A. a storage pool on Disk 2 and Disk 3
B. a spanned volume on Disk 2 and Disk 3
C. a mirrored volume on Disk 1 and Disk 3
D. a mirrored volume on Disk 2 and Disk 3
E. a RAID-5 volume on Disk 1, Disk 2, and Disk 3
F. a storage pool on Disk 1 and Disk 3
G. a spanned volume on Disk 0 and Disk 4
H. a mirrored volume on Disk 1 and Disk 4
Answer: D
QUESTION 186
You have a server that runs Windows Server 2012 R2.
The server contains the disks configured as shown in the following table.
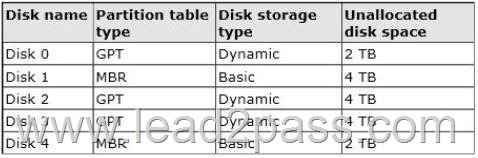
You need to create a volume that can store up to 3 TB of user files.
The solution must ensure that the user files are available if one of the disks in the volume fails.
What should you create?
A. A mirrored volume on Disk 1 and Disk 4
B. A storage pool on Disk 2 and Disk 3
C. A storage pool on Disk 1 and Disk 3
D. A mirrored volume on Disk 2 and Disk 3
Answer: D
A mirrored volume provides an identical twin of the selected volume. All data written to the mirrored volume is written to both volumes, which results in disk capacity of only 50 percent.
Any volume can be mirrored, including the system and boot volumes. The disk that you select for the shadow volume does not need to be identical to the original disk in size, or in its number of tracks and cylinders. This means that you do not have to replace a failed disk with an identical model. The unused area that you select for the shadow volume cannot be smaller than the original volume. If the area that you select for the shadow volume is larger than the original, the extra space on the shadow disk can be configured as another volume.
Dynamic disks provide features that basic disks do not, such as the ability to create volumes that span multiple disks (spanned and striped volumes) and the ability to create fault-tolerant volumes (mirrored and RAID-5 volumes).
The following operations can be performed only on dynamic disks:
Create and delete simple, spanned, striped, mirrored, and RAID-5 volumes.
Extend a simple or spanned volume.
Remove a mirror from a mirrored volume or break the mirrored volume into two volumes.
Repair mirrored or RAID-5 volumes.
Reactivate a missing or offline disk.
You need at least two dynamic disks to create a mirrored volume.
Mirrored volumes are fault tolerant and use RAID-1, which provides redundancy by creating two
identical copies of a volume.
Mirrored volumes cannot be extended.
Both copies (mirrors) of the mirrored volume share the same drive letter.
http://technet.microsoft.com/en-us/library/cc779765%28v=ws.10%29.aspx
http://msdn.microsoft.com/en-us/library/windows/desktop/aa363785%28v=vs.85%29.aspx
http://technet.microsoft.com/en-us/library/cc938487.aspx
QUESTION 187
Hotspot Question
Your network contains an Active Directory domain named adatum.com. All domain controllers run Windows Server 2012 R2. All client computers run Windows 7. The computer accounts for all of the client computers are located in an organizational unit (OU) named OU1. An administrator links a Group Policy object (GPO) to OU1. The GPO contains several application control policies.
You discover that the application control policies are not enforced on the client computers.
You need to modify the GPO to ensure that the application control policies are enforced on the client computers.
What should you configure in the GPO? To answer, select the appropriate service in the answer area.
Answer: 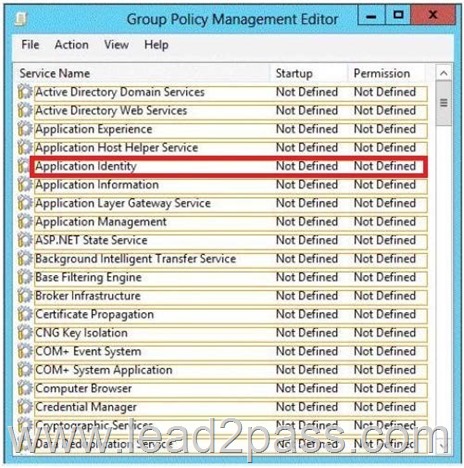
Explanation:
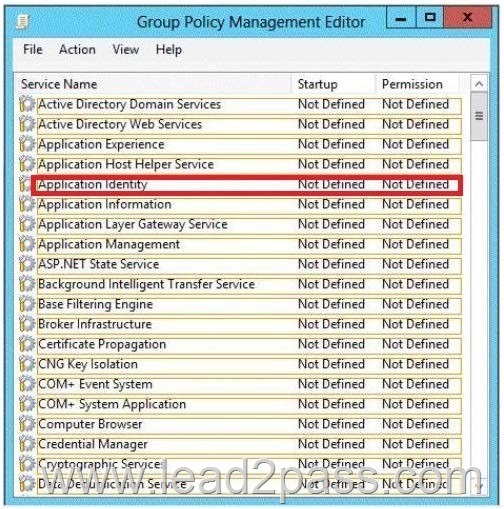
Does AppLocker use any services for its rule enforcement?
Yes, AppLocker uses the Application Identity service (AppIDSvc) for rule enforcement.
For AppLocker rules to be enforced, this service must be set to start automatically in the GPO.
http://technet.microsoft.com/en-us/library/ee619725%28v=ws.10%29.aspx
QUESTION 188
Your network contains an Active Directory domain named contoso.com.
The domain contains three servers named Server1, Served, and Server3.
You create a server group named ServerGroup1.
You discover the error message shown in the following exhibit. (Click the Exhibit button.)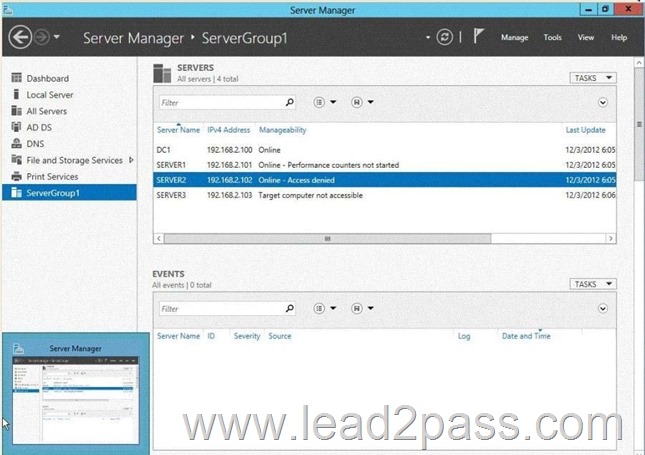
You need to ensure that Server2 can be managed remotely by using Server Manager.
What should you do?
A. On DC1, run the Enable-PSSessionConfiguration cmdlet.
B. On Server2, run the Add-Computer cmdlet.
C. On Server2/ modify the membership of the Remote Management Users group.
D. From Active Directory Users and Computers, add a computer account named Server2, and then restart Server2.
Answer: C
Explanation:
This is a security issue. To be able to access Server2 remotely through Server Manager the user need to be a member of the Remote Management Users group.
Note:
* Name: BUILTIN\Remote Management Users
Description: A Builtin Local group. Members of this group can access WMI resources over management protocols (such as WS-Management via the Windows Remote Management service). This applies only to WMI namespaces that grant access to the user.
* Enable-ServerManagerStandardUserRemoting
Provides one or more standard, non-Administrator users access to event, service, performance counter, and role and feature inventory data for a server that you are managing by using Server Manager.
Syntax:
Parameter Set: Default
Enable-ServerManagerStandardUserRemoting [-User] <String[]> [-Force] [-Confirm] [-WhatIf] [ <CommonParameters>]
Detailed Description
Provides one or more standard, non-Administrator users access to event, service, performance counter, and role and feature inventory data for a server that you are managing, either locally or remotely, by using Server Manager. The cmdlet must be run locally on the server that you are managing by using Server Manager. The cmdlet works by performing the following actions:
Adds access rights for specified standard users to the root\cimv2 namespace on the local server (for access to role and feature inventory information).
Adds specified standard users to required user groups (Remote Management Users, Event Log Readers, and Performance Log Readers) that allow remote access to event and performance counter logs on the managed server.
Changes access rights in the Service Control Manager to allow specified standard users remote access to the status of services on the managed server.
Incorrect:
Not A: the Enable-PSSessionConfiguration.This is an advanced cmdlet that is designed to be used by system administrators to manage customized session configurations for their users.
Reference: Enable-ServerManagerStandardUserRemoting
QUESTION 189
You have a server named Server1 that runs Windows Server 2012 R2.
Server1 has the Hyper-V server role installed. An iSCSI SAN is available on the network.
Server1 hosts four virtual machines named VM1, VM2, VM3, and VM4.
You create a LUN on the SAN.
You need to provide VM1 with access to the LUN. The solution must prevent other virtual machines from accessing the LUN.
What should you configure?
A. A fixed-size VHDX
B. A fixed-size VHD
C. A dynamically expanding VHD
D. A dynamically expanding VHDX
E. A pass-through disk
Answer: E
Explanation:
You can use physical disks that are directly attached to a virtual machine as a storage option on themanagement operating system. This allows virtual machines to access storage that is mapped directly to theserver running Hyper-V without first configuring the volume. The storage can be either a physical disk which isinternal to the server, or a SAN logical unit number (LUN) that is mapped to the server (a LUN is a logicalreference to a portion of a storage subsystem). The virtual machine must have exclusive access to thestorage, so the storage must be set in an Offline state in Disk Management. The storage is not limited insize, so it can be a multiterabyte LUN. When using physical disks that are directly attached to a virtual machine, you should be aware of the following:
This type of disk cannot be dynamically expanded.
You cannot use differencing disks with them.
You cannot take virtual hard disk snapshots.
Att:
If you are installing an operating system on the physical disk and it is in an Online state before the virtualmachine is started, the virtual machine will fail to start.
You must store the virtual machine configuration file inan alternate location because the physical disk is used by the operating system installation. For example,locate the configuration file on another internal drive on the server running Hyper-V.
http://technet.microsoft.com/en-us/library/ee344823%28v=ws.10%29.aspx http://blogs.technet.com/b/askcore/archive/2008/10/24/configuring-pass-through-disks-inhyper-v.aspx
QUESTION 190
Your network contains an Active Directory domain named contoso.com. The domain contains a print server named Server1 that runs Windows Server 2012 R2. Server1 contains a local group named Group1.
You share a printer named Printer1 on Server1.
You need to configure Printer1 to meet the following requirements:
– Ensure that the members of Group1, the Server Operators group, the Administrators group, and the Print Operators group can send print jobs to Printer1.
– Prevent other users from sending print jobs to Printer1.
Which two actions should you perform? (Each correct answer presents part of the solution. Choose two.)
A. Assign the Print permission to the Server Operators group
B. Remove the permissions for the Creator Owner group.
C. Remove the permissions for the Everyone group.
D. Assign the Print permission to Group1.
E. Assign the Print permission to the Administrators group.
Answer: CD
Explanation:
C: To prevent other users from sending print jobs to Printer1
D: To enable Group1 to send print jobs.
Note: The Server Operators group, the Administrators group, and the Print Operators group are all built-in and already have permissions to send print jobs.
QUESTION 191
You have a new server named Server1 that runs Windows Server 2012 R2. Server1 has two dual-core processors and 32 GB of RAM.
You install the Hyper-V server role on Server1.
You create two virtual machines on Server1 that each have 8 GB of memory.
You need to minimize the amount of time it takes for both virtual machines to access memory.
What should you configure on each virtual machine?
A. Resource control
B. Dynamic Memory
C. NUMA topology
D. Memory weight
Answer: C
Explanation:
* Dynamic Memory is a new Hyper-V feature that helps you use physical memory more efficiently. With Dynamic Memory, Hyper-V treats memory as a shared resource that can be reallocated automatically among running virtual machines. Dynamic Memory adjusts the amount of memory available to a virtual machine, based on changes in memory demand and values that you specify. Dynamic Memory is available for Hyper-V in Windows Server 2008 R2 Service Pack 1 (SP1).
* Dynamic Memory helps you use memory resources more efficiently. Before this feature was introduced, changing the amount of memory available to a virtual machine could be done only when the virtual machine was turned off. With Dynamic Memory, Hyper-V can provide a virtual machine with more or less memory dynamically in response to changes in the amount of memory required by the workloads or applications running in the virtual machine. As a result, Hyper-V can distribute memory more efficiently among the running virtual machines configured with Dynamic Memory. Depending on factors such as workload, this efficiency can make it possible to run more virtual machines at the same time on one physical computer.
Reference: Hyper-V Dynamic Memory Configuration Guide
QUESTION 192
Hotspot Question
Your network contains an Active Directory domain named contoso.com. Domain controllers run either Windows Server 2008 R2 or Windows Server 2012 R2. All client computers run Windows 8. All computer accounts are located in an organizational unit (OU) named OU1.
You create a Group Policy object (GPO) that contains several AppLocker rules.
You link the GPO to OU1.
You need to ensure that the AppLocker rules apply to all of the client computers.
What should you configure in the GPO? To answer, select the appropriate service in the answer area.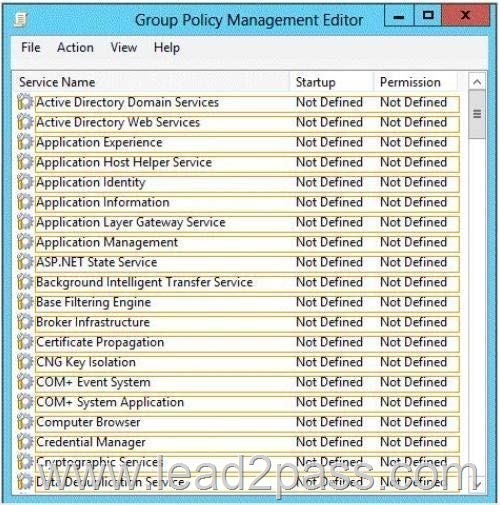
Answer:
QUESTION 193
Hotspot Question
Your network contains an Active Directory domain named contoso.com. Technicians use Windows Deployment Services (WDS) to deploy Windows Server 2012 R2. The network contains a server named Server1 that runs Windows Server 2012 R2. Server1 has the Hyper-V server role installed. You need to ensure that you can use WDS to deploy Windows Server 2012 R2 to a virtual machine named VM1.
Which settings should you configure?
To answer, select the appropriate settings in the answer area.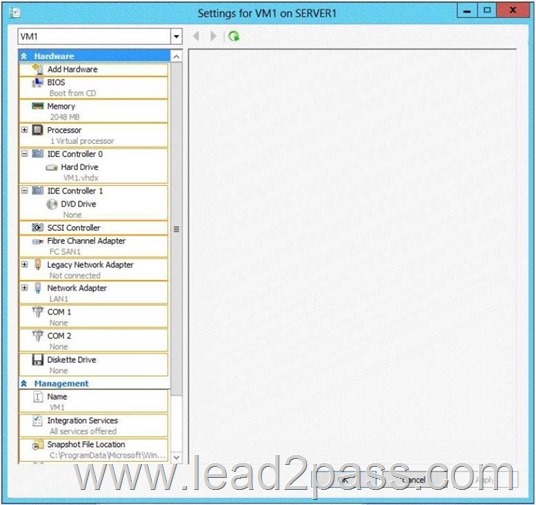
Answer: 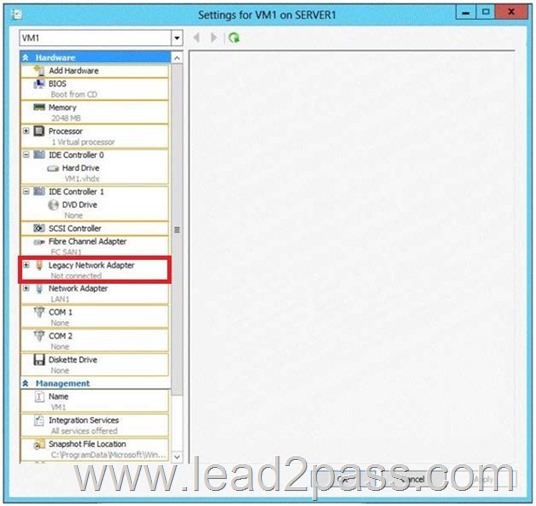
QUESTION 194
Hotspot Question
Your network contains an Active Directory domain named contoso.com.
The domain contains a member server named Hyperv1 and a domain controller named DC1.
Hyperv1 has the Hyper-V server role installed. DC1 is a virtual machine on Hyperv1.
Users report that the time on their client computer is incorrect.
You log on to DC1 and verify that the time services are configured correctly.
You need to prevent time conflicts between the time provided by DC1 and other potential time sources.
What should you configure? To answer, select the appropriate object in the answer area.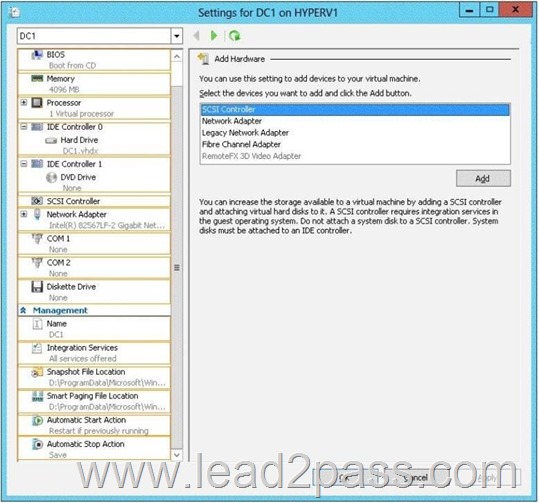
Answer: 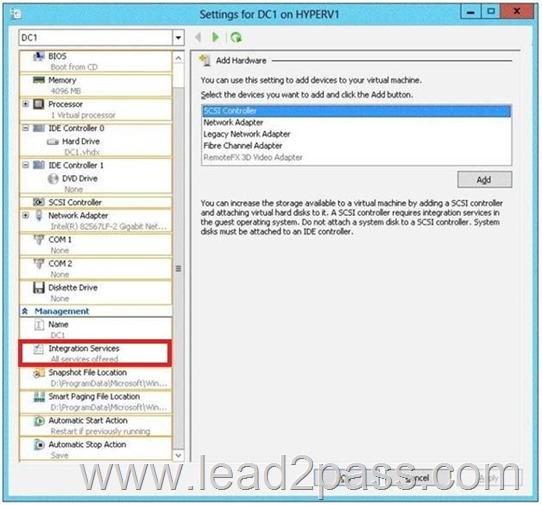
QUESTION 195
You perform a Server Core Installation of Windows Server 2012 R2 on a server named Server1.
You need to add a graphical user interface (GUI) to Server1.
Which tool should you use?
A. the dism.exe command
B. the Add-WindowsFeature cmdlet
C. the imagex.exe command
D. the setup.exe command
E. the ocsetup.exe command
F. the Add-WindowsPackage cmdlet
G. the Install-Module cmdlet
H. the Install-RoleService cmdlet
Answer: AB
Explanation:
Add-WindowsFeature -The Add-WindowsFeature cmdlet allows you to install specified roles, role services, and features on a computer that is running Windows Server 2008 R2.
Install-WindowsFeature -Installs one or more Windows Server roles, role services, or features on either the local or a specified remote server that is running Windows Server 2012 R2.
This cmdlet is equivalent to and replaces Add-WindowsFeature, the cmdlet that was used to install roles, role services, and features in Windows Server 2008 R2.
dism /online /get-features PS C:\> Install-WindowsFeature -Name Web-Server –
IncludeAllSubFeature -ComputerName Server1 -WhatIf
http://technet.microsoft.com/en-us/library/hh824822.aspx
http://technet.microsoft.com/en-us/library/dd744582(v=ws.10).aspx http://technet.microsoft.com/en-us/library/jj205467(v=wps.620).aspx
QUESTION 196
You have a server named Server1 that runs Windows Server 2012 R2.
Server1 has the Hyper-V server role installed.
You need to configure storage for a virtual machine to meet the following requirements:
– Support up to 3 TB of data on a single hard disk.
– Allocate disk space as needed.
– Use a portable storage format.
What should you configure?
A. A pass-through disk
B. A fixed-size VHD
C. A dynamically expanding VHD
D. A fixed-size VHDX
E. A dynamically expanding VHDX
Answer: E
Explanation:
http://technet.microsoft.com/en-us/library/hh831446.aspx
Support for virtual hard disk storage capacity of up to 64 TB.
vhd max is 2TB
QUESTION 197
Your network contains an Active Directory domain named contoso.com.
All user accounts are in an organizational unit (OU) named Employees.
You create a Group Policy object (GPO) named GP1.
You link GP1 to the Employees OU.
You need to ensure that GP1 does not apply to the members of a group named Managers.
What should you configure?
A. The Security settings of Employees
B. The WMI filter for GP1
C. The Block Inheritance option for Employees
D. The Security settings of GP1
Answer: D
Explanation:
A. Wrong Group
B. Windows Management Instrumentation (WMI) filters allow you to dynamically determine the scope of Group Policy objects (GPOs) based on attributes of the target computer.
C. Blocking inheritance prevents Group Policy objects (GPOs) that are linked to higher sites, domains, or organizational units from being automatically inherited by the child-level.
D. Set Managers to – Members of this security group are exempt from this Group Policy object.
Security settings.
You use the Security Settings extension to set security options for computers and users within the scope of a Group Policy object.
You can define local computer, domain, and network security settings.
Figure belows shows an example of the security settings that allow everyone to be affected by this GPO except the members of the Management group, who were explicitly denied permission to the GPO by setting the Apply Group Policy ACE to Deny. Note that if a member of the Management group were also a member of a group that had an explicit Allow setting for the Apply Group Policy ACE, the Deny would take precedence and the GPO would not affect the user.
http://technet.microsoft.com/en-us/library/bb742376.aspx
http://technet.microsoft.com/en-us/library/cc786636(WS.10).aspx
http://technet.microsoft.com/en-us/library/cc731076.aspx
http://technet.microsoft.com/en-us/library/cc779036(v=ws.10).aspx
QUESTION 198
You have a virtual machine named VM1.
You install Windows Server 2012 R2 on VM1.
You plan to use VM1 as an image that will be distributed to sales users to demonstrate the features of a custom application. The custom application only requires the Web Server (IIS) server role to be installed.
You need to ensure that the VHD file for VM1 only contains the required Windows Server 2012 R2 source files.
Which tool should you use?
A. dism.exe
B. ocsetup.exe
C. imagex.exe
D. servermanagercmd.exe
Answer: A
Explanation:
http://technet.microsoft.com/en-us/magazine/dd490958.aspx
You can use DISM to:
Add, remove, and enumerate packages and drivers.
Enable or disable Windows features.
Apply changes based on the offline servicing section of an unattend.xml answer file.
Configure international settings.
Upgrade a Windows image to a different edition.
Prepare a Windows PE image.
Take advantage of better logging.
Service down-level operating systems like Windows Vista with SP1 and Windows Server 2008.
Service all platforms (32-bit, 64-bit, and Itanium).
Service a 32-bit image from a 64-bit host and service a 64-bit image from a 32-bit host.
Make use of old Package Manager scripts.
QUESTION 199
Your network contains an Active Directory domain named contoso.com. The domain contains a server named Server1. Server1 runs Windows Server 2012 R2 and has the Hyper-V server role installed. On Server1, you create and start a virtual machine named VM1. VM1 is configured as shown in the following table.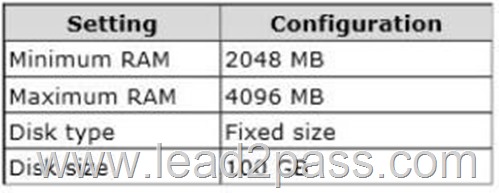
You plan to create a snapshot of VM1.
You need to recommend a solution to minimize the amount of disk space used for the snapshot of VM1.
What should you do before you create the snapshot?
A. Run the Stop-VM cmdlet.
B. Run the Convert-VHD cmdlet.
C. Decrease the Maximum RAM
D. Decrease the Minimum RAM.
Answer: A
Explanation:
What are virtual machine snapshots?
Virtual machine snapshots capture the state, data, and hardware configuration of a running virtual machine.
What are snapshots used for?
Snapshots provide a fast and easy way to revert the virtual machine to a previous state. For this reason, virtual machine snapshots are intended mainly for use in development and test environments. Having an easy way to revert a virtual machine can be very useful if you need to recreate a specific state or condition so that you can troubleshoot a problem.
There are certain circumstances in which it may make sense to use snapshots in a production environment. For example, you can use snapshots to provide a way to revert a potentially risky operation in a production environment, such as applying an update to the software running in the virtual machine.
How are snapshots stored?
Snapshot data files are stored as .avhd files. Taking multiple snapshots can quickly consume storage space. In the first release version of Hyper-V (KB950050) and in Hyper-V in Windows Server 2008 Service Pack 2, snapshot, snapshot data files usually are located in the same folder as the virtual machine by default. In Hyper-V in Windows Server 2008 R2, the files usually are located in the same folder as the virtual hard disk. The following exceptions affect the location of the snapshot data files: If the virtual machine was imported with snapshots, they are stored in their own folder. If the virtual machine has no snapshots and you configure the virtual machine snapshot setting, all snapshots you take afterwards will be stored in the folder you specify.
http://technet.microsoft.com/pt-pt/library/dd560637%28v=ws.10%29.aspx
Reducing the available RAM for the VM would reduce the size of the snapshot,what better than have the machine turn off, not using any memory
QUESTION 200
Your network contains an Active Directory domain named contoso.com.
The domain contains a file server named Server1 that runs Windows Server 2012 R2.
Server1 contains a shared folder named Share1. Share1 contains the home folder of each user.
All users have the necessary permissions to access only their home folder.
The users report that when they access Share1, they can see the home folders of all the users.
You need to ensure that the users see only their home folder when they access Share1.
What should you do from Server1?
A. From Windows Explorer, modify the properties of the volume that contains Share1.
B. From Server Manager, modify the properties of the volume that contains Share1.
C. From Server Manager, modify the properties of Share1.
D. From Windows Explorer, modify the properties of Share1.
Answer: C
Explanation:
http://technet.microsoft.com/en-us/library/cc784710(v=ws.10).aspx
Access based enumeration needs to be enabled:
If you want to get more 70-410 exam practice, please download the free New Version VCE Player from Lead2pass. By training the Lead2pass Microsoft 70-410 445q questions, you will pass the exam easily!