Lead2pass New Fortinet NSE4 PDF Dumps.v.2017-12-25.562q
https://www.lead2pass.com/nse4.html
QUESTION 534
View the Exhibit.
The administrator needs to confirm that FortiGate 2 is properly routing that traffic to the 10.0.1.0/24 subnet. The administrator needs to confirm it by sending ICMP pings to FortiGate 2 from the CLI of FortiGate 1. What ping option needs to be enabled before running the ping?
A. Execute ping-options source port1
B. Execute ping-options source 10.200.1.1.
C. Execute ping-options source 10.200.1.2
D. Execute ping-options source 10.0.1.254
Answer: D
QUESTION 535
How can you format the FortiGate flash disk?
A. Load the hardware test (HQIP) image.
B. Execute the CLI command execute formatlogdisk.
C. Load a debug FortiOS image.
D. Select the format boot device option from the BIOS menu.
Answer: D
QUESTION 536
How do you configure inline SSL inspection on a firewall policy? (Choose two.)
A. Enable one or more flow-based security profiles on the firewall policy.
B. Enable the SSL/SSH Inspection profile on the firewall policy.
C. Execute the inline ssl inspection CLI command.
D. Enable one or more proxy-based security profiles on the firewall policy.
Answer: AB
QUESTION 537
Which traffic sessions can be offloaded to a NP6 processor? (Choose two.)
A. IPv6
B. RIP
C. GRE
D. NAT64
Answer: AD
QUESTION 538
View the exhibit.
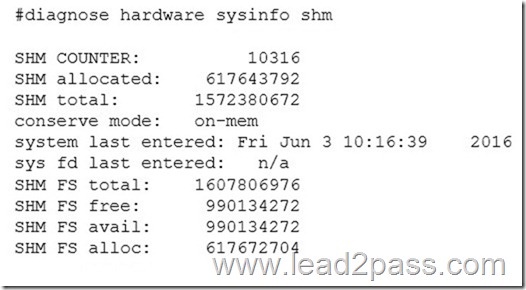
Based on this output, which statements are correct? (Choose two.)
A. FortiGate generated an event log for system conserve mode.
B. FortiGate has entered in to system conserve mode.
C. By default, the FortiGate blocks new sessions.
D. FortiGate changed the global av-failopen settings to idledrop.
Answer: BC
QUESTION 539
An administrator has blocked Netflix login in a cloud access security inspection (CASI) profile. The administrator has also applied the CASI profile to a firewall policy.
What else is required for the CASI profile to work properly?
A. You must enable logging for security events on the firewall policy.
B. You must activate a FortiCloud account.
C. You must apply an application control profile to the firewall policy.
D. You must enable SSL inspection on the firewall policy.
Answer: C
QUESTION 540
How does FortiGate look for a matching firewall policy to process traffic?
A. From top to bottom, based on the sequence numbers.
B. Based on best match.
C. From top to bottom, based on the policy ID numbers.
D. From lower to higher, based on the priority value.
Answer: A
QUESTION 541
How do you configure a FortiGate to do traffic shaping of P2P traffic, such as BitTorrent?
A. Apply an application control profile allowing BitTorrent to a firewall policy and configure a traffic shaping policy.
B. Enable the shape option in a firewall policy with service set to BitTorrent.
C. Apply a traffic shaper to a BitTorrent entry in the SSL/SSH inspection profile.
D. Apply a traffic shaper to a protocol options profile.
Answer: B
QUESTION 542
Which file names will match the *.tiff file name pattern configured in a data leak prevention filter? (Choose two.)
A. tiff.tiff
B. tiff.png
C. tiff.jpeg
D. gif.tiff
Answer: AD
QUESTION 543
An administrator has configured a dialup IPsec VPN with XAuth. Which method statement best describes this scenario?
A. Only digital certificates will be accepted as an authentication method in phase 1.
B. Dialup clients must provide a username and password for authentication.
C. Phase 1 negotiations will skip pre-shared key exchange.
D. Dialup clients must provide their local ID during phase 2 negotiations.
Answer: B
QUESTION 544
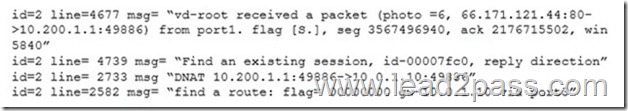
Examine this output from a debug flow:
Which statements about the output are correct? (Choose two.)
A. FortiGate received a TCP SYN/ACK packet.
B. The source IP address of the packet was translated to 10.0.1.10.
C. FortiGate routed the packet through port 3.
D. The packet was allowed by the firewall policy with the ID 00007fc0.
Answer: BC
QUESTION 545
Which component of FortiOS performs application control inspection?
A. Kernel
B. Antivirus engine
C. IPS engine
D. Application control engine
Answer: D
QUESTION 546
Which of the following statements about policy-based IPsec tunnels are true? (Choose two.)
A. They support GRE-over-IPsec.
B. They can be configured in both NAT/Route and transparent operation modes.
C. They require two firewall policies: one for each direction of traffic flow.
D. They support L2TP-over-IPsec.
Answer: BC
QUESTION 547
What statement describes what DNS64 does?
A. Converts DNS A record lookups to AAAA record lookups.
B. Translates the destination IPv6 address of the DNS traffic to an IPv4 address.
C. Synthesizes DNS AAAA records from A records.
D. Translates the destination IPv4 address of the DNS traffic to an IPv6 address.
Answer: B
NSE4 dumps full version (PDF&VCE): https://www.lead2pass.com/nse4.html
Large amount of free NSE4 exam questions on Google Drive: https://drive.google.com/open?id=0B3Syig5i8gpDeFZLNEJDeDRQdlE
You may also need:
NSE5 exam dumps: https://drive.google.com/open?id=0B3Syig5i8gpDOTJuU1o1TTliNVk